- ubuntu12.04环境下使用kvm ioctl接口实现最简单的虚拟机
- Ubuntu 通过无线网络安装Ubuntu Server启动系统后连接无线网络的方法
- 在Ubuntu上搭建网桥的方法
- ubuntu 虚拟机上网方式及相关配置详解
CFSDN坚持开源创造价值,我们致力于搭建一个资源共享平台,让每一个IT人在这里找到属于你的精彩世界.
这篇CFSDN的博客文章SQLSERVER对加密的存储过程、视图、触发器进行解密(推荐)由作者收集整理,如果你对这篇文章有兴趣,记得点赞哟.
加密测试的存储过程 。
|
1
2
3
4
5
6
7
8
9
10
11
12
|
IF EXISTS(
SELECT
1
FROM
SYSOBJECTS
WHERE
TYPE=
'P'
AND
NAME
=
'P_TEST'
)
DROP
PROCEDURE
P_TEST
GO
CREATE
PROCEDURE
P_TEST(@USERNAME
VARCHAR
(20),@MSG
VARCHAR
(20)
OUTPUT
)
WITH
ENCRYPTION
AS
BEGIN
IF(
SELECT
COUNT
(1)
FROM
Custs
WHERE
NAME
=@USERNAME)>0
SET
@MSG=
'此用户名存在'
ELSE
SET
@MSG=
'此用户名不存在'
END
|
解密的存储过程 。
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
|
Create
PROCEDURE
Decryption(@
procedure
sysname =
NULL
)
AS
SET
NOCOUNT
ON
DECLARE
@intProcSpace
bigint
, @t
bigint
, @maxColID
smallint
,@procNameLength
int
select
@maxColID =
max
(subobjid)
FROM
sys.sysobjvalues
WHERE
objid = object_id(@
procedure
)
--select @maxColID as 'Rows in sys.sysobjvalues'
select
@procNameLength = datalength(@
procedure
) + 29
DECLARE
@real_01 nvarchar(
max
)
DECLARE
@fake_01 nvarchar(
max
)
DECLARE
@fake_encrypt_01 nvarchar(
max
)
DECLARE
@real_decrypt_01 nvarchar(
max
),@real_decrypt_01a nvarchar(
max
)
declare
@objtype
varchar
(2),@ParentName nvarchar(
max
)
select
@real_decrypt_01a =
''
--提取对象的类型如是存储过程还是函数,如果是触发器,还要得到其父对象的名称
select
@objtype=type,@parentname=object_name(parent_object_id)
from
sys.objects
where
[object_id]=object_id(@
procedure
)
-- 从sys.sysobjvalues里提出加密的imageval记录
SET
@real_01=(
SELECT
top
1 imageval
FROM
sys.sysobjvalues
WHERE
objid =
object_id(@
procedure
)
and
valclass = 1
order
by
subobjid)
--创建一个临时表
create
table
#
output
( [ident] [
int
] IDENTITY (1, 1)
NOT
NULL
,
[real_decrypt] NVARCHAR(
MAX
) )
--开始一个事务,稍后回滚
BEGIN
TRAN
--更改原始的存储过程,用短横线替换
if @objtype=
'P'
SET
@fake_01=
'ALTER PROCEDURE '
+ @
procedure
+
' WITH ENCRYPTION AS select 1
/**//*'
+REPLICATE(
cast
(
'*'
as
nvarchar(
max
)), datalength(@real_01) /2 - @procNameLength)+
'*/'
else
if @objtype=
'FN'
SET
@fake_01=
'ALTER FUNCTION '
+ @
procedure
+
'() RETURNS INT WITH ENCRYPTION AS BEGIN RETURN 1
/**//*'
+REPLICATE(
cast
(
'*'
as
nvarchar(
max
)), datalength(@real_01) /2 - @procNameLength)+
'*/ END'
else
if @objtype=
'V'
SET
@fake_01=
'ALTER view '
+ @
procedure
+
' WITH ENCRYPTION AS select 1 as col
/**//*'
+REPLICATE(
cast
(
'*'
as
nvarchar(
max
)), datalength(@real_01) /2 - @procNameLength)+
'*/'
else
if @objtype=
'TR'
SET
@fake_01=
'ALTER trigger '
+ @
procedure
+
' ON '
+@parentname+
'WITH ENCRYPTION AFTER INSERT AS RAISERROR ('
'N'
',16,10)
/**//*'
+REPLICATE(
cast
(
'*'
as
nvarchar(
max
)), datalength(@real_01) /2 - @procNameLength)+
'*/'
EXECUTE
(@fake_01)
--从sys.sysobjvalues里提出加密的假的
SET
@fake_encrypt_01=(
SELECT
top
1 imageval
FROM
sys.sysobjvalues
WHERE
objid =
object_id(@
procedure
)
and
valclass = 1
order
by
subobjid )
if @objtype=
'P'
SET
@fake_01=
'Create PROCEDURE '
+ @
procedure
+
' WITH ENCRYPTION AS select 1
/**//*'
+REPLICATE(
cast
(
'*'
as
nvarchar(
max
)), datalength(@real_01) /2 - @procNameLength)+
'*/'
else
if @objtype=
'FN'
SET
@fake_01=
'CREATE FUNCTION '
+ @
procedure
+
'() RETURNS INT WITH ENCRYPTION AS BEGIN RETURN 1
/**//*'
+REPLICATE(
cast
(
'*'
as
nvarchar(
max
)), datalength(@real_01) /2 - @procNameLength)+
'*/ END'
else
if @objtype=
'V'
SET
@fake_01=
'Create view '
+ @
procedure
+
' WITH ENCRYPTION AS select 1 as col
/**//*'
+REPLICATE(
cast
(
'*'
as
nvarchar(
max
)), datalength(@real_01) /2 - @procNameLength)+
'*/'
else
if @objtype=
'TR'
SET
@fake_01=
'Create trigger '
+ @
procedure
+
' ON '
+@parentname+
'WITH ENCRYPTION AFTER INSERT AS RAISERROR ('
'N'
',16,10)
/**//*'
+REPLICATE(
cast
(
'*'
as
nvarchar(
max
)), datalength(@real_01) /2 - @procNameLength)+
'*/'
--开始计数
SET
@intProcSpace=1
--使用字符填充临时变量
SET
@real_decrypt_01 = replicate(
cast
(
'A'
as
nvarchar(
max
)), (datalength(@real_01) /2 ))
--循环设置每一个变量,创建真正的变量
--每次一个字节
SET
@intProcSpace=1
--如有必要,遍历每个@real_xx变量并解密
WHILE @intProcSpace<=(datalength(@real_01)/2)
BEGIN
--真的和假的和加密的假的进行异或处理
SET
@real_decrypt_01 = stuff(@real_decrypt_01, @intProcSpace, 1,
NCHAR
(UNICODE(
substring
(@real_01, @intProcSpace, 1)) ^
(UNICODE(
substring
(@fake_01, @intProcSpace, 1)) ^
UNICODE(
substring
(@fake_encrypt_01, @intProcSpace, 1)))))
SET
@intProcSpace=@intProcSpace+1
END
--通过sp_helptext逻辑向表#output里插入变量
insert
#
output
(real_decrypt)
select
@real_decrypt_01
--select real_decrypt AS '#output chek' from #output --测试
-- -------------------------------------
--开始从sp_helptext提取
-- -------------------------------------
declare
@dbname sysname
,@BlankSpaceAdded
int
,@BasePos
int
,@CurrentPos
int
,@TextLength
int
,@LineId
int
,@AddOnLen
int
,@LFCR
int
--回车换行的长度
,@DefinedLength
int
,@SyscomText nvarchar(
max
)
,@Line nvarchar(255)
Select
@DefinedLength = 255
SELECT
@BlankSpaceAdded = 0
--跟踪行结束的空格。注意Len函数忽略了多余的空格
CREATE
TABLE
#CommentText
(LineId
int
,Text nvarchar(255)
collate
database_default)
--使用#output代替sys.sysobjvalues
DECLARE
ms_crs_syscom
CURSOR
LOCAL
FOR
SELECT
real_decrypt
from
#
output
ORDER
BY
ident
FOR
READ
ONLY
--获取文本
SELECT
@LFCR = 2
SELECT
@LineId = 1
OPEN
ms_crs_syscom
FETCH
NEXT
FROM
ms_crs_syscom
into
@SyscomText
WHILE @@fetch_status >= 0
BEGIN
SELECT
@BasePos = 1
SELECT
@CurrentPos = 1
SELECT
@TextLength = LEN(@SyscomText)
WHILE @CurrentPos != 0
BEGIN
--通过回车查找行的结束
SELECT
@CurrentPos = CHARINDEX(
char
(13)+
char
(10), @SyscomText,
@BasePos)
--如果找到回车
IF @CurrentPos != 0
BEGIN
--如果@Lines的长度的新值比设置的大就插入@Lines目前的内容并继续
While (
isnull
(LEN(@Line),0) + @BlankSpaceAdded +
@CurrentPos-@BasePos + @LFCR) > @DefinedLength
BEGIN
SELECT
@AddOnLen = @DefinedLength-(
isnull
(LEN(@Line),0) +
@BlankSpaceAdded)
INSERT
#CommentText
VALUES
( @LineId,
isnull
(@Line, N
''
) +
isnull
(
SUBSTRING
(@SyscomText,
@BasePos, @AddOnLen), N
''
))
SELECT
@Line =
NULL
, @LineId = @LineId + 1,
@BasePos = @BasePos + @AddOnLen, @BlankSpaceAdded = 0
END
SELECT
@Line =
isnull
(@Line, N
''
) +
isnull
(
SUBSTRING
(@SyscomText, @BasePos, @CurrentPos-@BasePos + @LFCR), N
''
)
SELECT
@BasePos = @CurrentPos+2
INSERT
#CommentText
VALUES
( @LineId, @Line )
SELECT
@LineId = @LineId + 1
SELECT
@Line =
NULL
END
ELSE
--如果回车没找到
BEGIN
IF @BasePos <= @TextLength
BEGIN
--如果@Lines长度的新值大于定义的长度
While (
isnull
(LEN(@Line),0) + @BlankSpaceAdded +
@TextLength-@BasePos+1 ) > @DefinedLength
BEGIN
SELECT
@AddOnLen = @DefinedLength -
(
isnull
(LEN(@Line),0) + @BlankSpaceAdded)
INSERT
#CommentText
VALUES
( @LineId,
isnull
(@Line, N
''
) +
isnull
(
SUBSTRING
(@SyscomText,
@BasePos, @AddOnLen), N
''
))
SELECT
@Line =
NULL
, @LineId = @LineId + 1,
@BasePos = @BasePos + @AddOnLen, @BlankSpaceAdded =
0
END
SELECT
@Line =
isnull
(@Line, N
''
) +
isnull
(
SUBSTRING
(@SyscomText, @BasePos, @TextLength-@BasePos+1 ), N
''
)
if LEN(@Line) < @DefinedLength
and
charindex(
' '
,
@SyscomText, @TextLength+1 ) > 0
BEGIN
SELECT
@Line = @Line +
' '
, @BlankSpaceAdded = 1
END
END
END
END
FETCH
NEXT
FROM
ms_crs_syscom
into
@SyscomText
END
IF @Line
is
NOT
NULL
INSERT
#CommentText
VALUES
( @LineId, @Line )
select
Text
from
#CommentText
order
by
LineId
CLOSE
ms_crs_syscom
DEALLOCATE
ms_crs_syscom
DROP
TABLE
#CommentText
-- -------------------------------------
--结束从sp_helptext提取
-- -------------------------------------
--删除用短横线创建的存储过程并重建原始的存储过程
ROLLBACK
TRAN
DROP
TABLE
#
output
GO
启用DAC
SP_CONFIGURE
'remote admin connections'
;
GO
----0:仅允许本地连接使用 DAC,1:允许远程连接使用 DAC
SP_CONFIGURE
'remote admin connections'
, 0;
GO
RECONFIGURE
WITH
OVERRIDE;
GO
|
文件——>新建——>数据库引擎查询 。
服务器名称:admin:.或者admin:服务器名称 。
登录进去执行解密操作 。
|
1
2
3
|
USE TEST
EXEC
Decryption P_TEST
GO
|
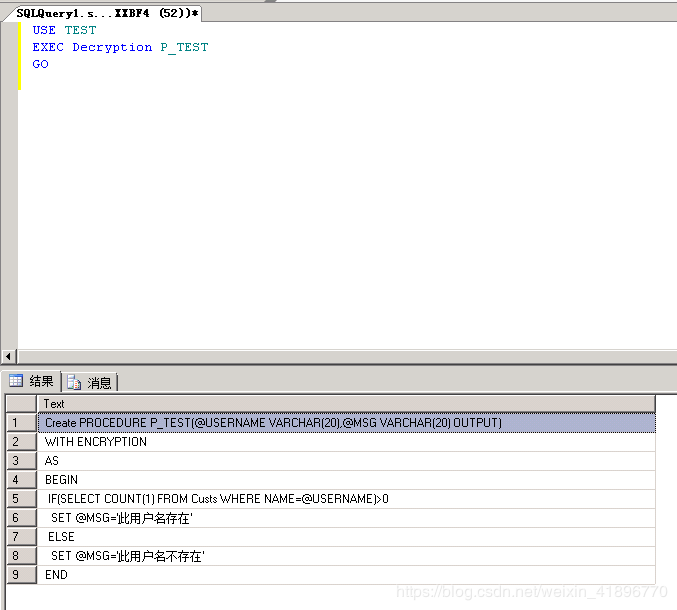
为了安全起见,不要在正式环境进行解密,避免在解密过程中将原存储过程损坏! 。
总结 。
以上所述是小编给大家介绍的SQLSERVER对加密的存储过程、视图、触发器进行解密,希望对大家有所帮助,如果大家有任何疑问请给我留言,小编会及时回复大家的。在此也非常感谢大家对我网站的支持! 如果你觉得本文对你有帮助,欢迎转载,烦请注明出处,谢谢! 。
原文链接:https://blog.csdn.net/weixin_41896770/article/details/103810177 。
最后此篇关于SQLSERVER对加密的存储过程、视图、触发器进行解密(推荐)的文章就讲到这里了,如果你想了解更多关于SQLSERVER对加密的存储过程、视图、触发器进行解密(推荐)的内容请搜索CFSDN的文章或继续浏览相关文章,希望大家以后支持我的博客! 。
我正在使用框架的对象编写一个用于加密/解密的简单库。方法如下: public static byte[] Encrypt(byte[] key, byte[] vector, byte[] input
据我所知,RIM Crypto API 似乎只提供用于对称加密 (3Des) 的 PKCS5 填充模式。我正在使用 JDE 4.6.0。 我正在尝试为黑莓应用程序提供密码学,该应用程序需要与已经使用标
我已经获得了用于加密的 Java 实现,但遗憾的是我们是一家 .net 商店,我无法将 Java 整合到我们的解决方案中。可悲的是,我也不是 Java 专家,所以我已经为此苦苦挣扎了几天,我想我终于可
我正在尝试使用 KMS 和 AWS 加密 SDK 加密数据。查看 AWS documentation 中提供的示例,似乎没有地方可以明确设置数据 key 。 我找到了 EncryptionMateri
我目前有一个用于为我的网站制作哈希的代码,该代码使用 SALT 进行哈希处理,因此密码是不可逆的...... 目前它是 100% 为我的网站工作,它是使用 ASP.NET(C#) 编码的 这是我的代码
我想要做的是在 javascript 中生成一个 key 对,并在 PHP 中使用这些加密,然后用 JS 解密。 我在附加的代码中有两个问题 它不会从装甲文本块重新加载私钥 并且它不会解密 PHP 加
在进行密码哈希时,我有以下 node.js 代码。 body.password = covid@19 salt = "hello@world" body.passwordhex = crypto.cr
我想知道的是在配置文件中加密连接字符串的明确方法。以下是我的问题: 使用机器级加密,访问我的服务器的任何人都不能编写一个小的 .Net 程序来读取连接字符串的内容吗? 如果我将我的应用程序部署到企业环
我知道 rsync 可以在文件传输期间启用/禁用 ssh 加密协议(protocol)。那么,如果 ssh 加密协议(protocol)被禁用了,是不是意味着 rsync 根本不做任何加密呢? 另外,
脚本必须搜索网页内的字符串。但该脚本不应显示它正在搜索的字符串。我的意思是搜索字符串应该采用加密格式或任何其他格式。但如果没有该搜索字符串,则不应显示网页或应在页面上显示错误。 我要开发一个插件。如果
我正在尝试加密 MySQL 上的某些字段。我正在使用 TPC-DS 的 v2.8 版本,并尝试在客户地址表的某些列上使用 AES。知道如何加密字段的所有行吗?我尝试使用 UPDATE customer
我需要一个简单的 javascript 函数,它允许我使用 key 加密 textarea 数据( key 是存储为散列 session 变量的用户密码,由 PHP 打印到字段中) 我基本上希望在用户
如何在 JavaScript 中散列/加密字符串值?我需要一种机制来隐藏 localStorage/cookie 中的一些数据吗? 这与安全问题有关,但我想为我的数据提供一些保护。 最佳答案 有很多
我有一个程序,其中数据库的密码由远程用户设置。该程序将用户名和密码保存到 xml 文件中的加密字符串中,否则应该是人类可读的。现在,这工作正常,我使用带有 key 的 C# DES 加密,它被加密和解
Kotlin 中是否有任何关于椭圆曲线加密的信息? 用于生成 key 对和加密、解密消息。 关于这个主题的信息很少甚至没有。 例如,我想实现 ECC P-521 椭圆曲线。 是否可以在 Kotlin
所以我知道 MD5 在技术上是新应用程序的禁忌,但我随机想到了这个: 自 md5($password); 不安全,不会 md5(md5($password)) 是更好的选择?我使用它的次数越多,它会变
我一直在努力使用 crypto_secretbox_easy() 在 libsodium 中加密/解密一些数据| .我似乎找不到关于使用的任何好的文档。 我想从用户那里获取密码,用它来以某种方式制作
我正在做一个加密项目 视频,我对这个程序有几个问题。 我用命令转码mp4至HLS与 ts段持续时间约为 10 秒。 首先,我需要使用数据库中的 key 加密这些视频。然而, 我不知道是否使用 ffmp
我有一个加密/复制保护问题。 我正在为使用加密狗的公司编写应用程序。请不要告诉我软件保护是没有用的,或者我应该让它自由地飞向空中,或者我花任何时间这样做都是浪费;这不是关于软件保护有效性的哲学问题,更
我对 有一个疑问VIM 加密 key . 我有一个文本文件,我使用加密该文件 :X 现在,加密 key 的存储位置(路径)。 无论是存储在单独的文件中还是存储在文本文件本身中。 如果我打开文件,它会询

我是一名优秀的程序员,十分优秀!