- html - 出于某种原因,IE8 对我的 Sass 文件中继承的 html5 CSS 不友好?
- JMeter 在响应断言中使用 span 标签的问题
- html - 在 :hover and :active? 上具有不同效果的 CSS 动画
- html - 相对于居中的 html 内容固定的 CSS 重复背景?
我想将我的应用程序连接到 KeyVault。通常,我可以创建一个新客户端 key 并在我的代码中使用它。
var _keyVaultClient = new KeyVaultClient(
async (string authority, string resource, string scope) =>
{
var authContext = new AuthenticationContext(authority);
var clientCred = new ClientCredential(clientId, clientSecret);
var result = await authContext.AcquireTokenAsync(resource, clientCred);
return result.AccessToken;
});
我可以创建一个new client secret来自 Azure 门户。
现在,我在 KeyVault 中找不到此选项。
在Program.cs中我有类似的东西
var keyVaultEndpoint = new Uri(Environment.GetEnvironmentVariable("VaultUri"));
configApp.AddAzureKeyVault(keyVaultEndpoint, new DefaultAzureCredential());
本地工作正常,但当我将应用程序部署到 Azure 时出现此错误:
Application '/LM/W3SVC/1699246683/ROOT' with physical root'C:\home\site\wwwroot' has exited from Program.Main with exit code ='0'. First 30KB characters of captured stdout and stderr logs:
[10:15:57 FTL] Host terminated unexpectedlyAzure.Identity.CredentialUnavailableException: DefaultAzureCredentialfailed to retrieve a token from the included credentials.
EnvironmentCredential authentication unavailable. Environmentvariables are not fully configured.
ManagedIdentityCredentialauthentication unavailable, no managed identity endpoint found.
SharedTokenCacheCredential authentication unavailable. No accountswere found in the cache.
at Azure.Identity.DefaultAzureCredential.GetTokenAsync(Boolean isAsync,TokenRequestContext requestContext, CancellationTokencancellationToken) atAzure.Identity.DefaultAzureCredential.GetTokenAsync(TokenRequestContextrequestContext, CancellationToken cancellationToken) atAzure.Security.KeyVault.ChallengeBasedAuthenticationPolicy.AuthenticateRequestAsync(HttpMessagemessage, Boolean async) atAzure.Security.KeyVault.ChallengeBasedAuthenticationPolicy.ProcessCoreAsync(HttpMessagemessage, ReadOnlyMemory
1 pipeline, Boolean async) at Azure.Core.Pipeline.RetryPolicy.ProcessAsync(HttpMessage message, ReadOnlyMemory1 pipeline, Boolean async) atAzure.Core.Pipeline.RetryPolicy.ProcessAsync(HttpMessage message,ReadOnlyMemory1 pipeline, Boolean async) at Azure.Core.Pipeline.HttpPipelineSynchronousPolicy.ProcessAsync(HttpMessage message, ReadOnlyMemory1 pipeline) atAzure.Core.Pipeline.HttpPipelineSynchronousPolicy.ProcessAsync(HttpMessagemessage, ReadOnlyMemory1 pipeline) at Azure.Core.Pipeline.HttpPipeline.SendRequestAsync(Request request, CancellationToken cancellationToken) at Azure.Security.KeyVault.KeyVaultPipeline.SendRequestAsync(Request request, CancellationToken cancellationToken) at Azure.Security.KeyVault.KeyVaultPipeline.GetPageAsync[T](Uri firstPageUri, String nextLink, Func1 itemFactory, StringoperationName, CancellationToken cancellationToken) atAzure.Core.PageResponseEnumerator.FuncAsyncPageable1.AsPages(String continuationToken, Nullable1 pageSizeHint)+MoveNext() atAzure.Core.PageResponseEnumerator.FuncAsyncPageable1.AsPages(String continuationToken, Nullable1pageSizeHint)+System.Threading.Tasks.Sources.IValueTaskSource<System.Boolean>.GetResult()at Azure.AsyncPageable1.GetAsyncEnumerator(CancellationToken cancellationToken)+MoveNext() at Azure.AsyncPageable1.GetAsyncEnumerator(CancellationTokencancellationToken)+MoveNext() atAzure.AsyncPageable1.GetAsyncEnumerator(CancellationToken cancellationToken)+System.Threading.Tasks.Sources.IValueTaskSource<System.Boolean>.GetResult() at Azure.Extensions.AspNetCore.Configuration.Secrets.AzureKeyVaultConfigurationProvider.LoadAsync() at Azure.Extensions.AspNetCore.Configuration.Secrets.AzureKeyVaultConfigurationProvider.LoadAsync() at Azure.Extensions.AspNetCore.Configuration.Secrets.AzureKeyVaultConfigurationProvider.Load() at Microsoft.Extensions.Configuration.ConfigurationRoot..ctor(IList1providers) atMicrosoft.Extensions.Configuration.ConfigurationBuilder.Build() atMicrosoft.Extensions.Hosting.HostBuilder.BuildAppConfiguration() atMicrosoft.Extensions.Hosting.HostBuilder.Build() atSkoruba.IdentityServer4.STS.Identity.Program.Main(String[] args) inC:\Projects\IdentityServer4\src\Skoruba.IdentityServer4.STS.Identity\Program.cs:line26Process Id: 13436. File Version: 13.1.20234.8. Description: IISASP.NET Core Module V2 Request Handler. Commit:c75b3f7a2fb9fe21fd96c93c070fdfa88a2fbe97
最佳答案
您正在使用 DefaultAzureCredential,它将部署时常用的身份验证凭据与开发环境中用于身份验证的凭据结合起来。 DefaultAzureCredential 将尝试按顺序通过以下机制进行身份验证。 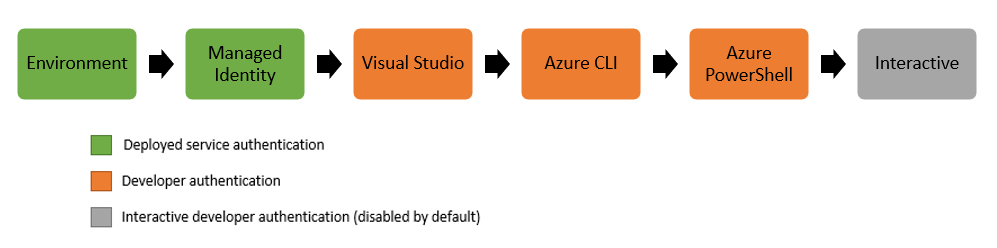
它在您本地工作的原因很可能是它能够使用本地盒子(上面的橙色盒子)进行身份验证。
现在,对于已部署的环境,您需要执行以下操作之一:
或者,2. 在 Environment Variables 中设置客户端凭据(例如,如果是 Web 应用程序,则在应用程序设置中)。
关于c# - Azure KeyVault : how to create clientId and clientSecret?,我们在Stack Overflow上找到一个类似的问题: https://stackoverflow.com/questions/64260687/
我正在尝试找到某种方法将我的证书从一个 Azure 订阅中的 Key Vault 移动到另一个 Azure 订阅。有没有办法这样做> 最佳答案 下面是一种移动 Azure Key Vault 中创建的
在 ARM 模板中,我想在预先存在的 KeyVault 中写入一个 secret - 我尚未将其创建为当前模板的一部分。 我正在使用此代码 { "dependsOn": [
我在 VSTS 中使用以下 Azure Powershell 命令。 (Get-AzureKeyVaultSecret -vaultName "debugkv" -name "CoreConfig-S
这两个库似乎有相似的目的:安全地存储和控制对 token 、密码、API key 和其他 secret 的访问。 我一直在使用 Microsoft.Azure.KeyVault 并取得了一些成功,不是
我最近开始将 Microsoft.Azure.KeyVault 命名空间中的旧 Azure KeyVault 客户端替换为 Azure.Security.KeyVault 中的新客户端。 在获取 se
我最近开始将 Microsoft.Azure.KeyVault 命名空间中的旧 Azure KeyVault 客户端替换为 Azure.Security.KeyVault 中的新客户端。 在获取 se
我目前正在使用 Azure SDK for Go。一切都很顺利,直到我遇到以下问题: keyVault, err := client.Get(context.Background(), "NAME_O
我正在 Azure 中部署虚拟机。用户名和密码是自动创建的,并在部署时作为参数传递。部署虚拟机的资源组也作为参数传递,因此可以是任何内容。 我的Keyvault位于特定资源组中,虚拟机的用户名和密码应
这是一个与 keyvault 相关的问题。我在 keyvault 中存储了 pfx 证书(带有私钥)。从我的服务主体中,我尝试访问 keystore 以获取证书。我正在编写以下代码来检索 pfx 证书
我正在尝试配置 Key Vault 值的定期刷新。我由 Visual Studio 生成的原始代码如下所示 var keyvaultEndpoint = new Uri($"https://{vaul
我正在尝试配置 Key Vault 值的定期刷新。我由 Visual Studio 生成的原始代码如下所示 var keyvaultEndpoint = new Uri($"https://{vaul
我使用下面的代码从 Azure Key Vault 获取证书 private X509Certificate2 GetClientCertificate(string thumbprint)
我使用下面的代码从 Azure Key Vault 获取证书 private X509Certificate2 GetClientCertificate(string thumbprint)
创建新的 KeyVault 时出现以下错误 The subscription is not registered to use namespace 'Microsoft.KeyVault' 对于所有其
我们最近发现自己需要将每个 secret (名称和值)从一个 Azure KeyVault 复制到新创建的一个。我找到了从备份中恢复 secret 的方法,但我们没有备份。是否有一个 Powershe
我正在使用 .net core 2.1 和 OpenIdConnect 以及以下 AccessPolicies 创建 azure keyvault AccessPolicies = new List
与 Azure CLI一个使用 az keyvault secret 显示 读取 secret 值。 Azure Powershell/Az.KeyVault是怎么做到的? ? 我已尝试GetAzKe
与 Azure CLI一个使用 az keyvault secret 显示 读取 secret 值。 Azure Powershell/Az.KeyVault是怎么做到的? ? 我已尝试GetAzKe
2 个不同的租户(租户 A 中的订阅 A 和租户 B 中的订阅 B) 我们在 Azure 云中有一个订阅,并且我们已经设置了 Azure Keyvault。我们可以在那里创建 key 并使用其中一个
只是想知道如何使用新的 Azure.Security.KeyVault 库实现相同的目标: Azure.Security.KeyVault.Certificates https://learn.mic

我是一名优秀的程序员,十分优秀!